Weaponized Intelligence: How Gamma AI Is Exploited for Credential Harvesting in Cloud Environments
Exposing the Rise of AI-Generated Phishing in the Cloud: How Adversaries Weaponize Gamma AI to Bypass Trust and Breach Defenses
Introduction
In 2025, artificial intelligence (AI) tools are more accessible and powerful than ever. Among these, Gamma AI—an advanced large language model (LLM) capable of mimicking human dialogue and rendering high-fidelity content—has emerged not only as a productivity asset but also as a new weapon in the arsenal of cyber attackers. This article examines how Gamma AI is being misused to conduct large-scale credential harvesting attacks, particularly in cloud environments, by generating fake login portals that deceive users and evade traditional security filters.
This article offers:
Real-world Gamma AI abuse cases
Technical analysis of AI-generated phishing portals
Expanded understanding of JavaScript weaponization
Detection strategies for enterprise defenders
Visual, tabular, and code-based evidence of abuse
1. Anatomy of a Gamma AI-Enabled Attack
Step 1: Reconnaissance & Prompt Engineering
Attackers begin by crafting highly specific prompts to exploit Gamma AI’s generative strengths. With a prompt like:
"Generate an HTML version of the Microsoft 365 login page with embedded JavaScript error handling and brand-accurate styles."
Gamma AI is tricked into producing nearly identical replicas of real corporate login portals. Crucially, the attackers are not just cloning appearance—they are flipping the intent of JavaScript components within these models. The JavaScript medium—originally designed for enhancing interactivity—is repurposed here to:
Capture keystrokes silently
Create time-delayed fake redirects
Fake successful logins to delay detection
Gamma AI doesn’t understand the malicious context; it simply optimizes output to match the prompt’s request. This abstraction layer is what makes the misuse so difficult to detect.
Step 2: Deployment via Cloud Infrastructure
Attackers deploy these AI-generated phishing pages using public cloud services (S3 buckets, Azure Blobs, Google Functions) with weak or misconfigured access policies. A widespread issue is the default public-read settings on certain objects. Attackers exploit this to:
Host malicious JavaScript and HTML directly
Circumvent perimeter detection (HTTPS over trusted domains)
Auto-scale attacks using CI/CD pipelines and disposable subdomains
Step 3: Credential Harvesting
Gamma AI-written phishing emails are crafted using behavioral mirroring. These emails include personalized sender names, real calendar formatting, and even mimic user signatures to increase trust. Once users are directed to the phishing portal and submit credentials, JavaScript keyloggers or form captures send the data via encrypted webhooks.
Step 4: Post-Harvest Exploitation
Harvested credentials are used to:
Create persistent sessions through OAuth tokens
Create inbox rules to hide future alerts
Spread laterally using shared documents or compromised Teams environments
Trigger MFA fatigue attacks where AI mimics help desk responses
How to Spot the Fakes:
Look for generic or slightly off domain names (e.g.,
m1crosoft-auth365.com)Hover over login buttons and verify HTTPS destination
Watch for pixel-perfect UI but with minor behavior deviations (e.g., error messages that do not match your company's style)
2. Timeline of Notable Gamma AI Misuse Cases
DateIncident SummarySourceJan 202440+ cloud tenants in North America targeted by AI-generated Google login clonesCISA BulletinApr 2024Phishing-as-a-Service (PhaaS) kit containing Gamma AI templates detected on GitHubTrend MicroJul 2024AWS S3 public buckets traced back to AI-generated Microsoft 365 phish kitsCheck PointOct 2024Financial firm breach tied to Gamma AI-generated Zoom and Okta portalsCrowdStrike
This timeline reveals a disturbing trend: attackers are continuously refining tactics using LLMs like Gamma AI. They move quickly, update templates frequently, and mask activity using content obfuscation techniques only possible through model-powered generation.
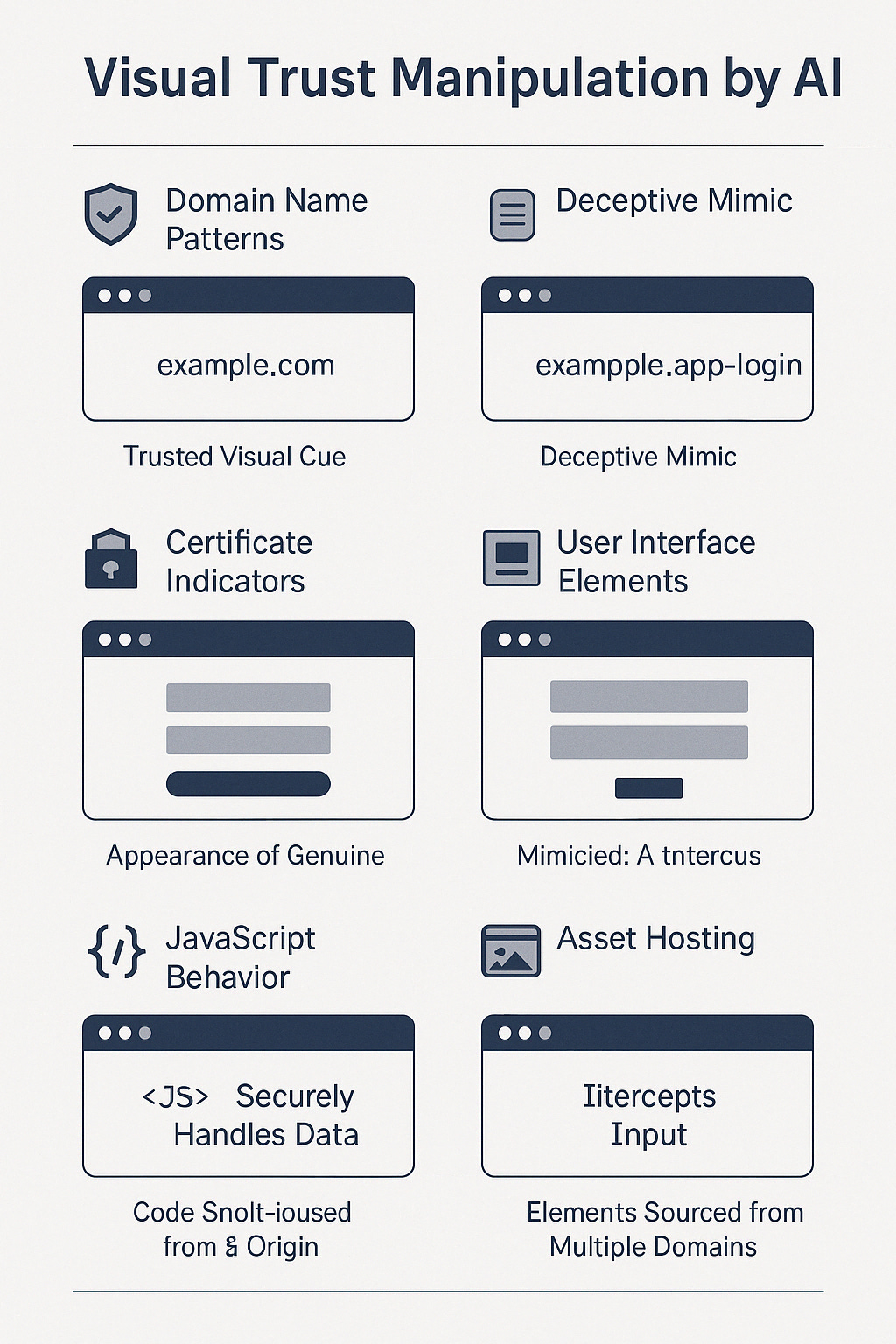
3. Infographic: How AI Mimics Login Portals
Visual Analysis Components:
Comparison of authentic and AI-generated UIs
Code snippets showing legitimate vs Gamma AI login JavaScript (note use of
onblurcapture events)Examples of copied but slightly modified branding (e.g., font spacing, favicon variants)
How Users Can Detect Fakes:
If a login page does not refresh on failed login, or lacks secondary authentication prompts
If branding elements like logos load from non-Microsoft or Google URLs
If the text formatting is overly perfect or lacks regional grammar nuances
4. Table: Cloud Vulnerabilities Exploited by AI Phishing Kits
Cloud ServiceVulnerabilityDescriptionTactic Used (MITRE)AWS S3Public Bucket ExposureMisconfigured S3 buckets allow external hosting of malicious pagesTA0001, TA0006Azure BlobAnonymous Access EnabledBlob storage set to allow anonymous GETsTA0043Google CloudFunction URL Deployment without AuthAttackers host malicious scripts in cloud functions with public accessTA0002, TA0006Office365OAuth Token AbuseCompromised credentials used to abuse OAuth scopes for persistenceTA0001, TA0004
Preventive Advice:
Conduct regular audits of storage container policies
Use WAF (Web Application Firewall) with script fingerprinting to detect unusual HTML or JavaScript patterns
Require signed URLs or token validation for all public content access
5. Evidence Matrix: TTPs Per MITRE ATT&CK
Misuse PatternTacticTechniqueGamma AI RolePhishing page generationInitial AccessT1566.002 (Spearphishing via link)Generates fake login interfacesCredential harvesting via JavaScript hooksCollectionT1056.001 (Keylogging)Embeds keyloggers or token capture JavaScriptLateral Movement via OAuth abuseLateral MoveT1550.001 (Application Access)AI-generated emails mimic admin change requestsEvasion via polymorphic emailsDefense EvasionT1036.004 (Masquerading)Rewrites headers/footers to evade detection heuristics
This matrix links the creativity of Gamma AI prompts directly to abuse tactics, bridging the cognitive leap needed to understand how LLMs affect security baselines.
6. How Gamma AI Bypasses Traditional Filters
Language Obfuscation: Dynamic wording and use of idioms confuse pattern-based detection models.
Header Randomization: Gamma AI alters metadata in ways that fool DMARC checks.
Style Perfectionism: Absence of typos and consistent sentence complexity trick basic phishing classifiers.
JavaScript Cloaking: Embeds logic inside encoded scripts or loads it asynchronously to bypass sandbox emulators.
How to Spot These Patterns:
Scrutinize spelling that’s too perfect
Check message headers in your email client
Use browser dev tools to examine script origin (e.g.,
login.jshosted fromcdn-login-secure.netis a red flag)
7. Real-World Case Study: PhishHub-247
Background: In July 2024, dark web marketplace PhishHub-247 launched a PhaaS toolkit branded as "Gamma AI Enhanced."
Functionality:
30+ auto-updating fake cloud login templates
JavaScript modules copied from real vendor SDKs
AI-powered fake chatbots to delay incident reporting
Impact:
8,000+ credentials stolen from high-trust domains in education and finance
Fake login pages adjusted per target region and browser language
Lessons for Defenders:
Monitor for high fidelity replication of internal systems
Track AI-generated subdomain patterns across cloud edge logs
8. Checklist: Cloud AI Security Hardening
Disable all anonymous access to blob and object storage
Enforce signed URL usage for file access
Implement Zero Trust segmentation using reverse proxy solutions
Enable behavioral phishing detection in email gateways
Audit and restrict OAuth scope access per app
Train users to identify subtle mismatches in interface behavior
9. Detection Script (Python): Identify AI-Generated Phishing HTML
from bs4 import BeautifulSoup
import re
suspicious_phrases = ["Generated by OpenAI", "ai-generated", "Prompted to generate"]
style_classes = ["login-box", "form-container", "error-msg", "centered-login"]
html_file = "sample_phishing_page.html"
with open(html_file, "r") as file:
soup = BeautifulSoup(file, "html.parser")
flags = 0
for phrase in suspicious_phrases:
if phrase.lower() in soup.text.lower():
print(f"Suspicious text found: {phrase}")
flags += 1
for tag in soup.find_all(True):
if any(cls for cls in style_classes if cls in tag.get("class", [])):
print(f"Suspicious class usage: {tag}")
flags += 1
if flags == 0:
print("No obvious AI generation traces found.")
else:
print(f"{flags} AI indicators detected.")
10. Internal Alert Template for SecOps
Subject: Urgent — Possible AI-Generated Phishing Attempt Detected
Body:
Team,
We've detected a phishing attempt that appears to leverage Gamma AI to produce a cloned login page. It bypassed initial filters and mimics our M365 interface almost perfectly.
Immediate Actions:
- Quarantine affected devices and user accounts
- Notify users listed in the IOCs for credential reset
- Escalate incident to Tier 2 with reference: GAMAI-365-CLOAK
--SecOps
Conclusion
Gamma AI illustrates the double-edged nature of powerful LLMs. While transformative in business use, they become dangerous multipliers in threat actors’ toolkits. By hijacking JavaScript's purpose, repurposing model outputs for phishing, and bypassing security heuristics, attackers are rewriting the rules of deception.
Organizations must evolve detection strategies, reduce trust boundaries, and adapt training to the new era of AI-enhanced phishing. Knowing the signs—UI perfection, behavioral mismatches, unexpected script origins—can turn human intuition into your best last-mile defense.
We must act not only with vigilance, but with vision. Because in a world where fake is indistinguishable from real, only layered strategy and constant adaptation can protect your cloud perimeter.